日本語
毎日 通常購入しなくては使用できないソフトウエアを無料で提供します!
Ultima Steganography 1.5< のgiveaway は 2011年2月21日
本日の Giveaway of the Day
ウェブカメラとマイクを簡単にオン/オフにしてプライバシーを保護します。
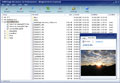
Ultima Steganographyは大変簡単に使用できるWindows用のプログラムで、ファイルを暗号化して写真内に隠すことが可能。
ファイルが写真内にイメージとして隠されると通常のイメージのように写真として表示され、高度な安全性を提供。Ultima Steganographyでファイルを安全に管理。
必要なシステム:
Windows XP/ Vista/ 7
出版社:
Enplase Researchホームページ:
http://enplase.com/pages/Ultima+Steganography+description.htmlファイルサイズ:
3.11 MB
価格:
$24
他の製品
GIVEAWAY download basket
Developed by Hewlett-Packard
Developed by Kaspersky Lab
The standard anti-malware solution for Windows.
Recover lost or forgotten passwords for RAR files.
iPhone 本日のオファー »
$29.99 ➞ 本日 無料提供
$3.99 ➞ 本日 無料提供
$7.99 ➞ 本日 無料提供
Outfit gives recommendations on what to wear for cycling and running outdoors in different weather conditions.
$2.99 ➞ 本日 無料提供
$10.99 ➞ 本日 無料提供
Android 本日のオファー »
Introducing the new generation of math learning apps powered by handwritten digit recognition.
$2.99 ➞ 本日 無料提供
$0.49 ➞ 本日 無料提供
$2.99 ➞ 本日 無料提供
A math learning game with fun and engaging gameplay and as we all know learning through play and fun is more effective.
$2.99 ➞ 本日 無料提供
$0.49 ➞ 本日 無料提供


コメント Ultima Steganography 1.5
Please add a comment explaining the reason behind your vote.
Wire FX: It is sad to hear people suggest that only those doing something illegal would have a reason to hide something. I suppose you also feel that people should not have locks on the front door of their homes since as long as they have nothing illegal in their house, why not leave it open for anyone who feels like walking in?
Seriously - I know that I have a lot of things which I would want to keep secret and secured but none of it is illegal or even morally questionable. Now some of it could not be protected with this software but some of it would work well with s/w of this type.
Even just simple stuff like passwords - we are told to have different passwords for every account, to choose things which are random so they can't be guessed and change them often - I don't know about you, but for me that would be dozens of random passwords changed frequently, the idea of having a nice list hidden in, say, my desktop wallpaper so I can check it as I need to but others would not even know it is there - well, if this s/w is quick enough to be practical, then there is a good example of it's morally acceptable and legal use.
Save | Cancel
Here's how to hide files in an image without using any software:
http://www.sizlopedia.com/2008/01/23/how-to-hide-important-files-inside-a-picture/
Save | Cancel
@ Wire FX:
Since you're talking about "ethics" and legality in combination with encryption, I feel sorry for you, you're CLUELESS!
You don't have a clue about the extend of today's spying in every sector, including industrial spying, patents, personal data etc.
The only reason someone might not be advised to use such a software for sensitive data, is that it won't protect you enough. This is also true for software costing thousands (the vast majority of such software).
Save | Cancel
Wirefx: We wear clothes in public because some things are best kept private. That is also why letters are sent in envelopes. It is wise to secure data traversing the Intranet, where security is so poor that it can be regarded as "public". Steganography is one way of doing that.
cmmr: While that technique would fall within the definition of "steganography", the more usual technique is to hash the file to be hidden and then change the least significant digits to encode that within the image file acting as a receptacle. That usually has minimal impact on file size, but requires that the file to be hidden is no larger than about 4% of the size of the image, for a 24-bit image.
Trucker: One additional way to secure one's copyright on pictures is to add a copyright notice using steganography. Since most stealers of pictures are too lazy even to edit them, that can be useful proof of theft.
One trouble with adding data to images is that it can readily be stripped out when even minor changes are made to the image.
Save | Cancel
I would enthusiastically endorse this were it not for the fact that Enplase code quality is low and that they missed the point of steganography, which is that it should be undetectable. The name of the file which you're hiding and its description are not encrypted, at least not by your key, therefor they are detectable. When you decrypt, your key is visible.
The install is clean. Bugs that were noted last time appear to be fixed, but you should always check that the encrypted file unencrypts correctly. Interestingly, this exposed a bug in the Windows 7 Windows Photo Viewer, it's not displaying large JPEG files correctly, as verified by other photo viewers (the color saturation or luminosity is off).
I recommend reading my comments #19 and #43 from the August 22, 2010 giveaway, noting that some of the bugs mentioned last time appear to be fixed.
Lossless operations can be performed on the result images. I recommend running PNG files through a PNG optimizer, you can easily cut the result file sizes in half without affecting the encrypted data. Large files can obviously be split and the pieces encrypted in multiple images.
Save | Cancel